Introduction to SSH and Encryption [Beginners]
Learn how encryption works and to connect Git with GitHub using SSH
Suppose you have a program installed on your computer that prompts for a password every time you do CTRL + S. What about entering the password every time you push or pull from GitHub? Wouldn't that be tiring and frustrating?
You may say, "Yes, it is but that's how secure systems work!" and that's true it is done to protect your work but it also gets into your way of productivity.
SSH takes away the woes of such monotonous tasks so you can spend time actually coding which is the most interesting part of your journey.
What is SSH?
It is a network protocol that allows the user to execute command line instructions securely on a remote computer.
Almost like a tunnel through which your data/instruction gets transmitted to another computer without allowing anyone in between to interrupt it.
It protects against the risk of any unauthorized access, data theft, impersonation, and message tampering and many more such vulnerabilities.
To understand how SSH works, we first need to have a look at how do computers communicate with each other.
How do computers communicate
A computer can talk to each other through secure connections that are backed by cryptographic algorithms.
There are three most common secure connections models:
- Symmetric Encryption
- Asymmetric Encryption
- Hashing
Let's talk about each of them in a little bit of detail:
(i). Symmetric Encryption: In this connection, if the client and the host computers have the same key, they can communicate with each other. This key is like a secret software that only you and I have that converts the message into gibberish and converts the gibberish back into an understandable message.
So, the client can encrypt the data using the key before sending it to the host. Then upon the arrival of the message, the host can decrypt it to read the message.
But the problem with this kind of connection is anyone with the same key can gain access to our data which can be dangerous at times!
So to avoid such scenarios we have a better version of encryption called asymmetric encryption.
(ii). Asymmetric encryption: This is a strongly encrypted connection that is theoretically almost impossible to break. It is based on a key exchange algorithm called Diffie Hellman Algorithm
In this connection, both the client and the host will have two keys:
- A private key that is never shared with anyone
- A public key that is always used to connect with others
Public keys can only encrypt the data and the private key can only decrypt the data.
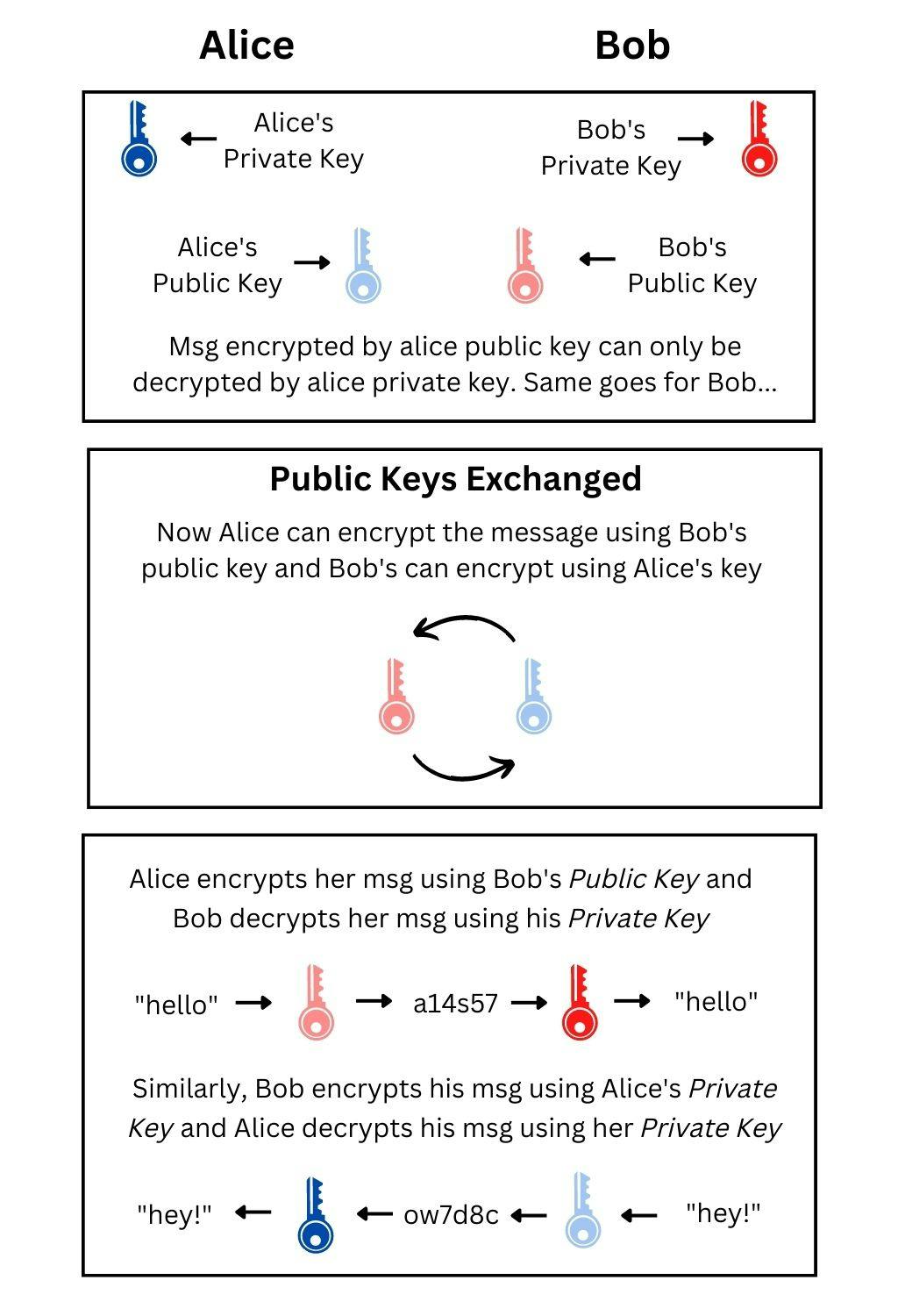
Example: If Alice wants Bob to read her message she must encrypt her message through bob's public key before sending it to him. On receiving the message, Bob will use his private key to decrypt and read her message.
Diffie Hellman Algorithm (Optional)
Good to know but you can skip this topic
It is a mathematical key exchange algorithm that is used in the field of cryptography and is implemented heavily in computer science as well.
In fact, you are currently reading this blog which is stored somewhere on the site servers and your computer has connected to site servers through the Diffie Hellman algorithm.
Suppose we have two parties a client and a host computer who want to connect with each other. This can be better understood by a diagram:
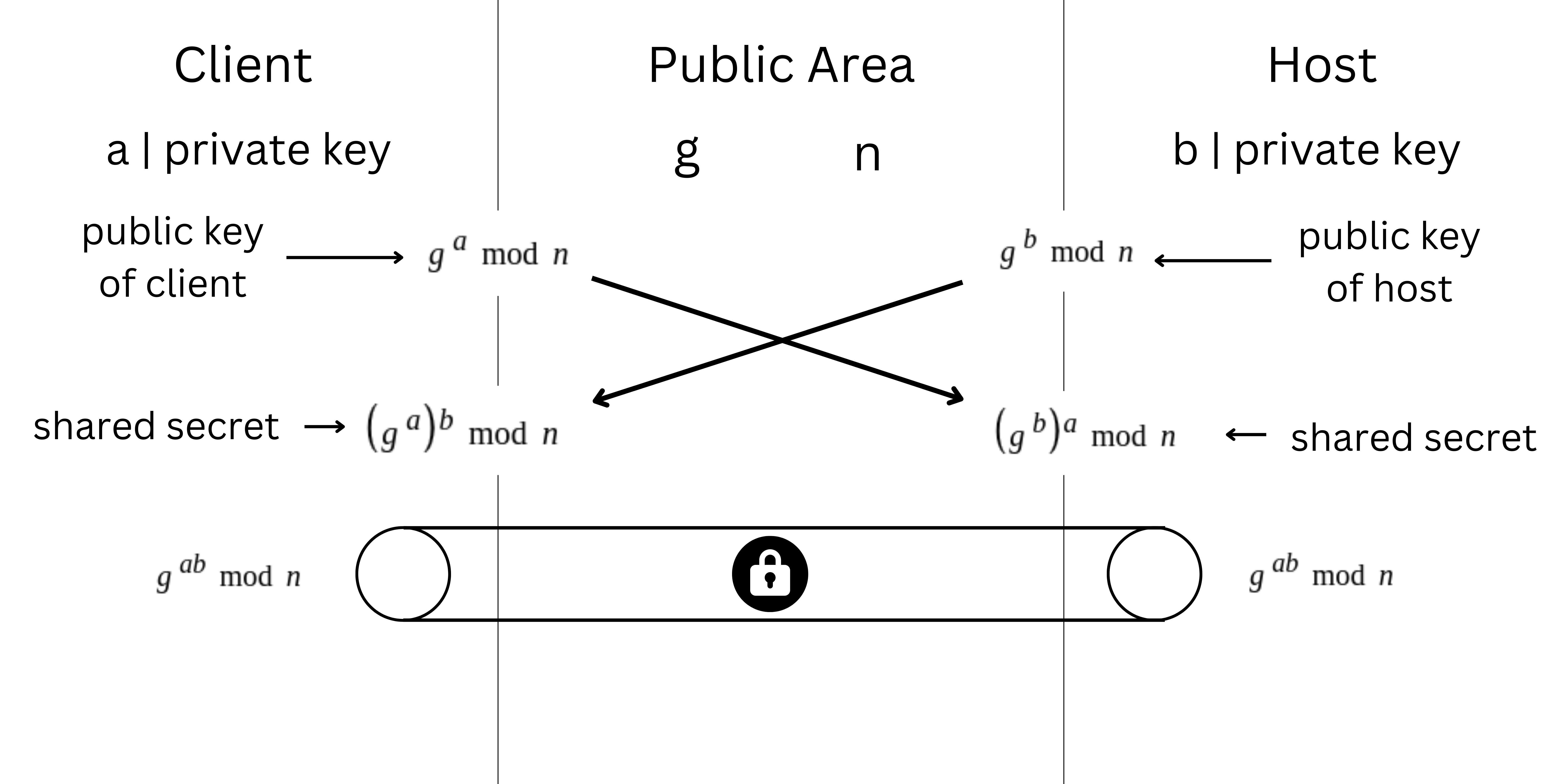
Public Area is where the client and host have agreed upon some conditions. For an attacker who wants to break into this secure connection, he needs to use these variables somehow to find out the users private key but that's super difficult as of now!
First, understand what are these alphabets and what they signify:
g - is usually a small prime number
n - is a 4096 bits large number
a & b - are secret numbers
The private key is mixed with the public variables to generate a public key that can be shared with other computers as it is hard to derive the value of 'a' through the value of the public key.
How the client's computer connects:
The client's private key is 'a' so his computer finds the value of $$ g ^ a \mod n $$ which makes up his public key that can be shared with any computer willing to connect.
When the public keys are exchanged and the client gets the public key of the host that is: $$ (g ^ b \mod n) $$ as the host's private key is 'b'.
The client's computer somehow through complex calculations is able to calculate the shared secret key by mixing his own private key with the host's public key : $$ ((g^b)^a \mod n) = (g^{ab} \mod n) $$ (Note: This is not the exact calculation. It is made simple to keep it understandable)
How the host's computer connects:
Everything is the same for the host. His private key is 'b' so his public key will be: $$ g ^ b \mod n $$ Host receives the client's public key which is: $$ g ^ a \mod n $$ as his private key is 'a'. The host's computer mixes his private key with the client's public key to find out the shared secret key: $$ (g ^ b)^a \mod n = g ^ {ab} \mod n$$
Now when both parties have the same shared secret key they can connect with each other and transmit the data freely. No attacker can interrupt them as he will need the private keys of both the host and the client to break into their conversation which is impossible for now. Sorry hackers! :(
(iii). Hashing: This is one more advanced step to tighten up the security of your connection. This is done mainly to make sure that no one tampered with the message.
Hashing functions use three things: The message, the shared secret key*, and the data packet number. It takes these three items as inputs and outputs a hash code.
Hash is generated once before the message is sent by the client and then again when the message is received by the host. If both hashes are not the same then the message has been changed by someone.
Okay fine, that's a lot of irrelevant talks you have included you just tell me how the SSH works. That's it!
How SSH works?
It is a more smart and powerful network protocol using the power of different encryption techniques. SSH generates temporary private and public keys for a connection. The public keys are exchanged with each other using asymmetric encryption A shared secret key is generated using the public key of the host. The client and the host are connected only when they have the same key Basically, SSH combines these two techniques symmetric and asymmetric encryption to build a strong network connection.
This is sometimes known as 'Hybrid Encryption' mentioned on many sites and in video lectures. So without the earlier discussion of asymmetric and symmetric encryption, you wouldn't be able to understand how SSH works this easily.
That's a lot to grasp. You just tell mean how to connect my Git with GitHub using SSH to show off my friends.
Connecting Git using SSH
To demonstrate this I created a simple text file and I will push it to my private repository using the command line. I have Linux operating system, if you have any other OS you can look for a suitable video on youtube.
I copied the SSH of my repo and added a new remote with the SSH of the repo. Then I tried to push the files in the master branch to GitHub
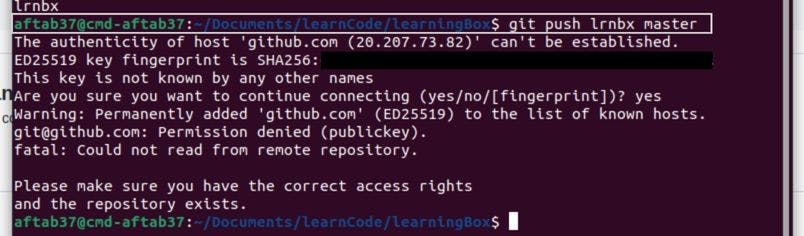
Did of all of this to avail nothing! :(
To make the push command work first we need to create the SSH key and save it in our GitHub profile settings:
Word of Caution: Copy the content of id_rsa.pub not the content of id_rsa which is meant to be never shared with anyone!
- Go to your ~/.ssh directory or create one if you don't have it.
- Generate an SSH key using this command: ssh-keygen -C "Write your comment"
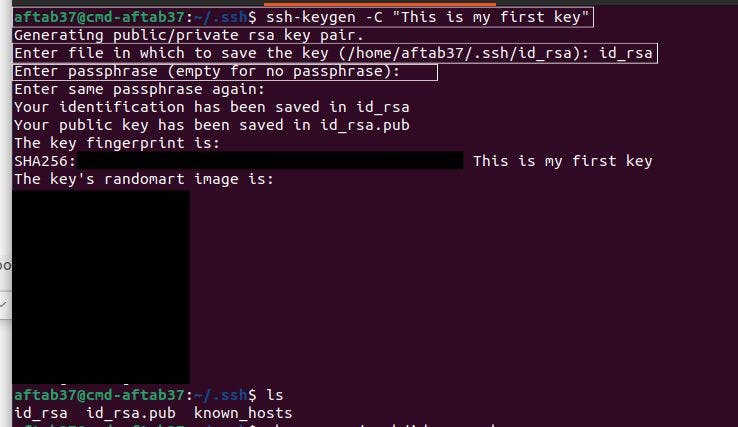
- Enter where you want to store your key
- You can enter a passphrase (I will pass)
- Open and copy the content of your id_rsa.pub file.
- Open GitHub.com and go to profile settings
- Go to 'SSH and GPG keys' under the header 'Access'
- Click on the new SSH key button
- Put the title, set the key type to an authentication key, and at last paste the inside the key field. Click add SSH key button.
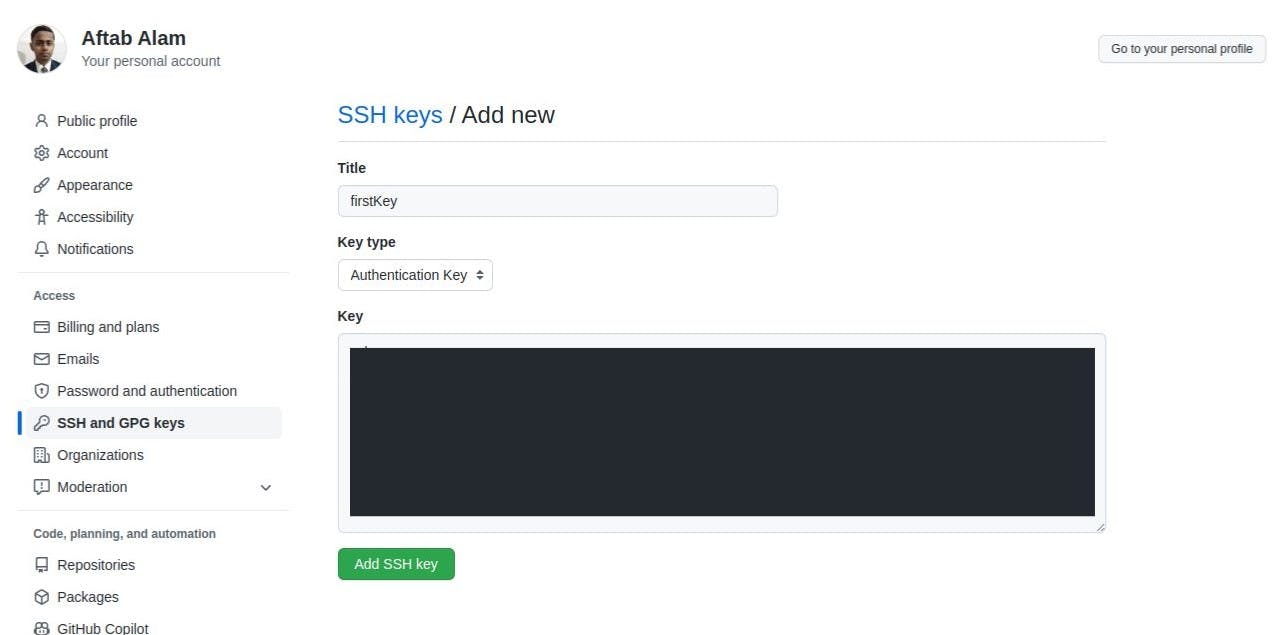
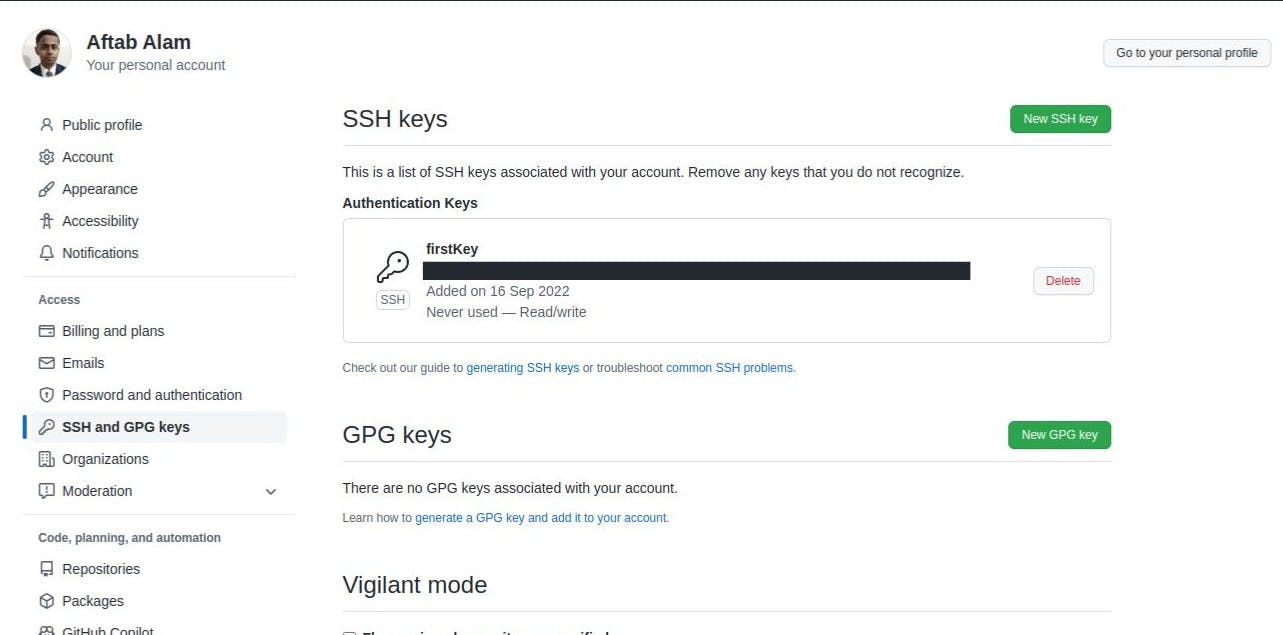
It will look like this with the text 'Never used - Read/Write' just after adding the key:
When you push some file through SSH into your repo the key will turn green and show the last usage of that key.
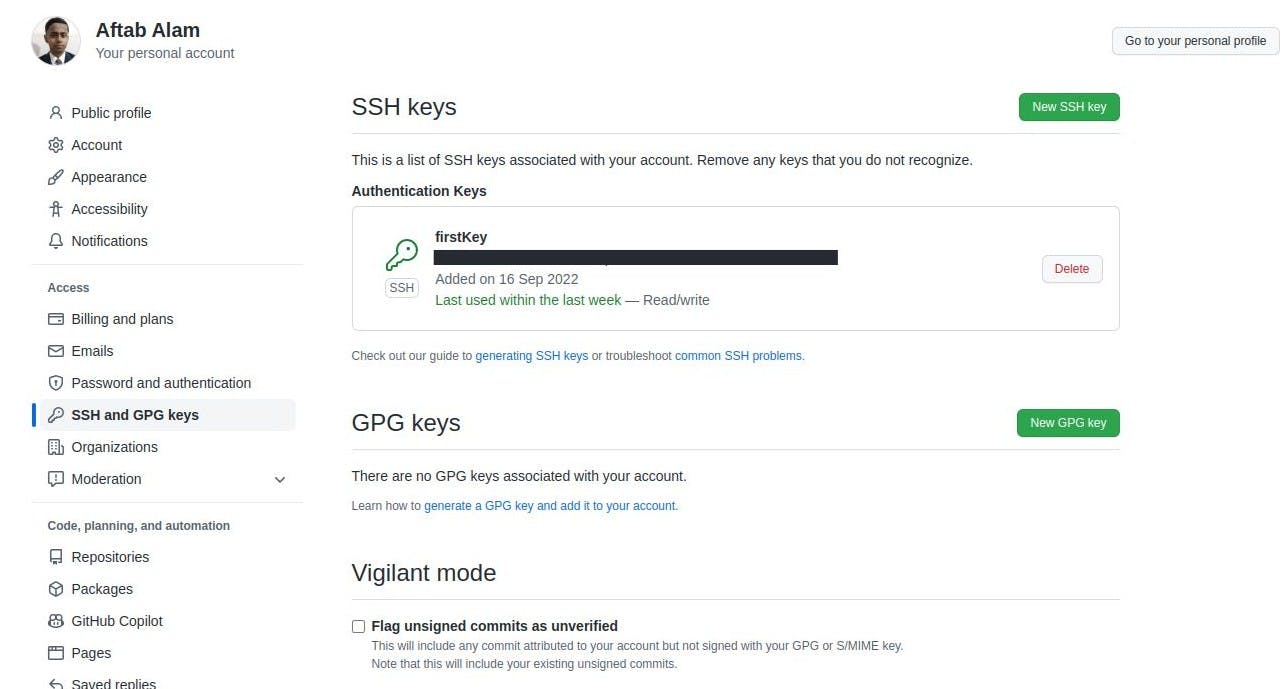
Now try to push the file to your GitHub and it should work now.
That's it for today! If you liked this article please share it with your friends!
![Introduction to SSH and Encryption [Beginners]](https://cdn.hashnode.com/res/hashnode/image/upload/v1663482924622/iqcJ-XAAh.jpg?w=1600&h=840&fit=crop&crop=entropy&auto=compress,format&format=webp)